Copiers

May 29, 2025
In a world of constant tech updates, few partnerships have truly stood the test of time. That’s why we’re...

December 7, 2023
Printer Vulnerability Multifunction printers (MFPs) are pivotal tools within contemporary offices, optimizing...

December 7, 2023
Network Vulnerability Due to Printers In the modern business landscape, network printers play an integral...

December 5, 2023
Overlooked Printer Security In today’s digital age, where data breaches and cybersecurity threats...

November 29, 2023
Network Security in the Age of IoT In today’s digital age, where data security is a paramount concern...
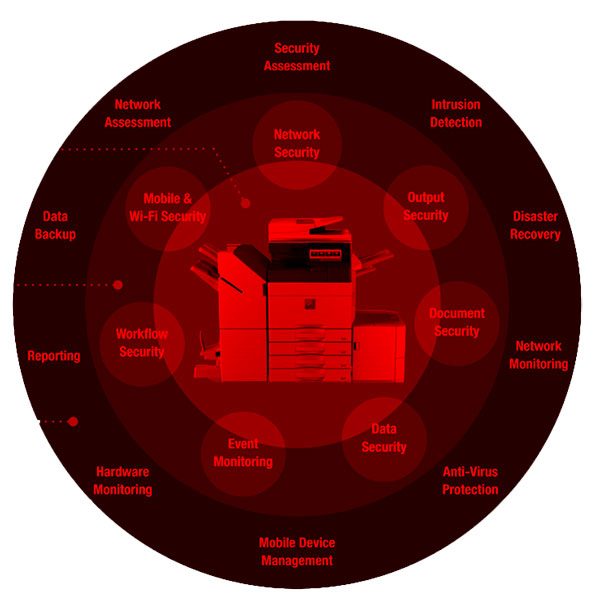
September 26, 2023
Information transfer is a significant part of business and organizational communications in today’s...
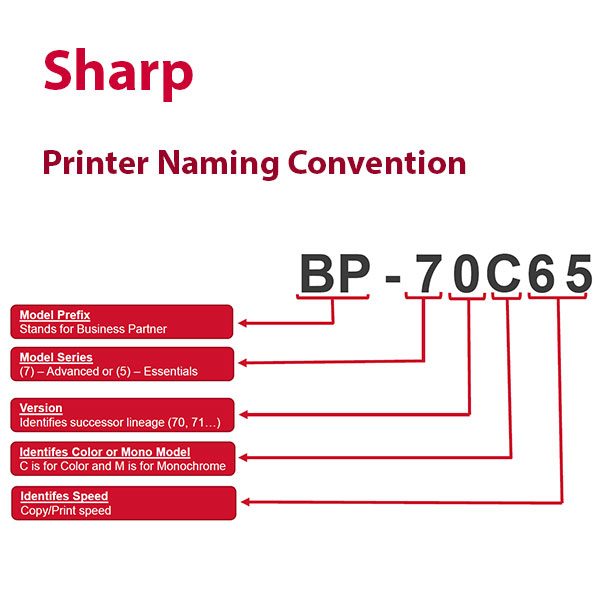
May 4, 2023
What is a product nomenclature? According to David Loshin in Information Management, a nomenclature system...

May 31, 2022
We have full warehouses in each of our 9 locations. with common items like laptops, laptop accessories,...

March 21, 2022
ATTENTION: Security changes for Google (Gmail users) can cause your Multi-function printer to lose the...

November 30, 2021
Would you like to start saving more money? First, it’s a major energy saver to print double-sided in...

February 1, 2021
Sharp multifunction devices and printers from Les Olson Company helped enhance the healthcare organization's...
No posts found


