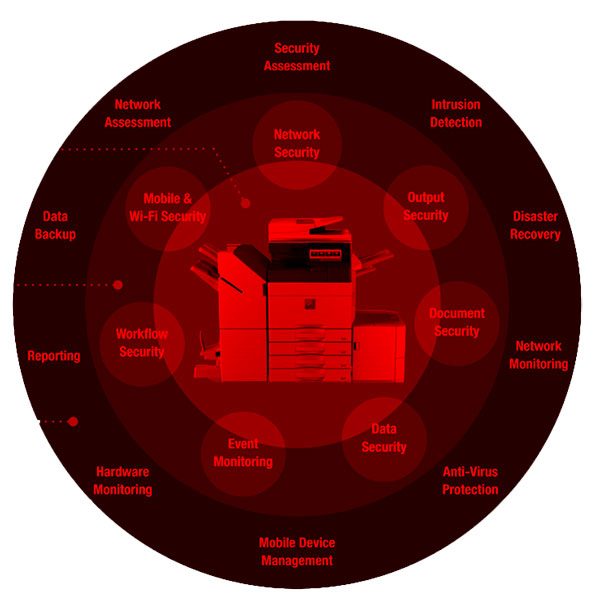
Information transfer is a significant part of business and organizational communications in today’s digital age. Mobile and cloud integrations with office technologies increase the complexity and frequency of protecting business information. Corporate information, customer data, client privacy, and financial information are constantly under threat by interception and misuse. Data security is critical for businesses of all sizes. Sensitive information and company records require protection for business continuity and reduced risk exposure. This blog article examines the need for businesses to incorporate printer security into their office data security plan and how Sharp Printers can help meet an organization’s Cybersecurity needs.
Why Information Security Is Important
According to the Institute of Internal Auditors, cybersecurity, IT governance, and information security is the most significant business risk in 2023.1 The average data breach cost was $4.35 million in 2022. Healthcare has been the costliest breach for the past 12 consecutive years, costing an average of $10.1 million in 2022.2 Around 47% of American adults have had their data exposed by cyber thieves.3 Information security is essential for protecting the confidentiality, integrity, and availability of data and system operations. It underpins trust in digital interactions and economic stability. As the digital landscape continues to evolve, the importance of information security will increase.

Monitoring Printer Security
While companies invest heavily in securing their computer networks and data centers, one often overlooked area of vulnerability is the humble office printer. Sharp, a renowned name in the world of office equipment, recognizes the importance of printer security. Sharp developed a range of features to provide complete protection. This comprehensive guide will explore 15 Sharp printer features that address various aspects of information security in a business environment.

Why Printer Security is Important
Before delving into the specific security features, it’s crucial to understand why printer security matters for businesses. Printers have evolved from simple devices that produce hard copies to sophisticated multifunction devices that can scan, copy, fax, and email documents. These capabilities introduce new security risks with severe consequences if not addressed.
Data Breaches
Unsecured printers can be a gateway for data breaches. Print tasks of sensitive information, such as financial documents or customer data, are vulnerable to interception and theft. Compromised data offers cyberthieves the information they need to extort companies and their customers.
Compliance Requirements
Many industries are subject to strict data protection regulations like GDPR, HIPAA, or CCPA. Failure to secure printed documents can lead to non-compliance and hefty fines. Specific regulations and compliance requirements related to data protection and privacy impose protections for the public and organizations. Information security ensures that organizations comply with these regulations, avoiding legal penalties.
Corporate Espionage
Competitors or malicious actors may exploit unsecured printers to access proprietary information or trade secrets. Printer security safeguards sensitive and confidential data from unauthorized access, ensuring that sensitive information remains confidential. This security breach includes personal data, financial records, intellectual property, and trade secrets.
Reputation Damage
A data breach can cause reputational damage and loss of trust among customers and partners. Security breaches severely damage an organization’s reputation. Customers and stakeholders expect responsible and secure handling of their sensitive data. A breach leads to a loss of trust and customers moving to competitors.
Operational Disruption
Security incidents can disrupt business operations and lead to costly downtime. A recent example of an expensive business disruption is the hack of MGM Resorts International and Caesars Entertainment. The catastrophe included ATMs, slot machines, room digital key cards, and electronic payment systems. Caesars reported that their breach involved a customer database, including driver’s licenses and social security numbers. These outages went on for days, disrupting business operations and customer services. Losses are in the millions.4

An Overall IT Cybersecurity Strategy Includes Printer Security
A cyber breach affects many different areas of an organization. It may impact company employees, company proprietary information, enterprise operations, organizational partners, and customer data. The risk of what can be lost and disrupted is too high. Printer security is an integral part of an organization’s overall Cybersecurity Strategy. Sharp recognizes this need and develops robust security features to protect businesses from potential threats. These security features listed below are paramount for business stability.
 15 Security Features That Provide Comprehensive Protection
15 Security Features That Provide Comprehensive Protection
Sharp printers offer a wide array of security features that collectively provide comprehensive protection for businesses and organizations. Many technologies deploy in tandem, working together to thwart cybercriminals and protect company data. Sharp incorporates 15 security features to safeguard printer users, as outlined below.
#1 Data Security in Transit or at Rest
Data security is a multifaceted concern and Sharp addresses it comprehensively with encryption for data transmission and storage.
- Data Encryption: Sharp printers support encryption protocols, such as SSL/TLS, to secure data during transmission over the network.
- Hard Drive Encryption: Sharp’s hard drive encryption protects data stored on the printer’s internal storage is protected. This protection is especially critical for printers with storage capabilities, as it prevents unauthorized access to stored documents.
#2 Data Security Kit (DSK) and Common Criteria Certification/ISO-15408
Sharp offers a Data Security Kit (DSK) that enhances the security of printers. This data security includes an overwrite function and common criteria certification to meet rigorous global security standards.
- Overwrite Function: DSK includes an overwrite function that erases residual data on the printer’s hard drive, making it nearly impossible for unauthorized users to recover sensitive information.
- Common Criteria Certification: Sharp printers have achieved Common Criteria Certification (ISO-15408), an internationally recognized security standard. This certification assures that the printer meets stringent security requirements.
#3 Data and Information Security
Sharp’s commitment to data security extends beyond printed pages. Stored files and folders receive encryption. Printed sensitive documents require authentication for release.
- File and Folder Encryption: The ability to encrypt files and folders on the printer’s storage ensures that even if someone gains physical access to the device, they cannot easily access sensitive data.
- Secure Printing: Secure printing options allow users to send print jobs to the printer but require authentication at the device before the document releases for printing. This at-the-device authentication prevents unauthorized individuals from picking up confidential documents.
#4 Access Control Security
Access control is a fundamental aspect of printer security. Restricting access to sensitive information ensures that only designated personnel view confidential data.
- User Authentication: Sharp printers support authentication methods like PIN codes or proximity cards, ensuring only authorized personnel can use the device.
- Role-Based Access: Administrators can define roles and permissions for users, limiting access to specific features or functions based on their job responsibilities.
#5 Data Security at End-of-Lease
When a printer reaches the end of its lease or lifecycle, it’s crucial to ensure that no sensitive data remains on the device. Old office equipment is a favorite data source for cyberthieves. Protecting information is critical from birth to grave.
- Data Overwrite: Sharp printers have a data overwrite feature that securely erases all data from the hard drive, rendering it unrecoverable.
- Return Procedures: Sharp provides guidelines and procedures for securely returning leased or retired devices, minimizing the risk of data exposure.
#6 Data Security During Operation
Security isn’t static; it requires maintenance during a printer’s operational life. Any lapse in data security is an exploitation opportunity for cyber hackers.
- Firmware Updates: Sharp regularly releases firmware updates, including security patches, to address known vulnerabilities. These updates reduce the risk of firmware attacks and malicious intrusions.
- Remote Monitoring: Sharp’s remote monitoring tools allow IT administrators to monitor printer security settings and quickly respond to suspicious activity.
- Authority Groups: Sharp has built-in authority groups to manage and restrict copying, printing, and scanning to safeguard data.
- Active Directory Groups: Printer administrators can apply directory groups to most Sharp printers to control print driver settings and configurations.
- Confidential Printing: Sharp MFPs provide a function to keep confidential documents secure through assigned PIN codes to selected employees.
- 256-bit Data Encryption: Sharp’s information encryption combined with up to 10 times data overwrite ensures the protection of customer data.
- Sharp Application Whitelisting: Sharp MFPs have whitelisting features to protect against unofficial software and application updates.
#7 Authentication, Authorization, and Restriction
Sharp printers offer robust authentication, authorization, and restriction capabilities. These functions limit unwanted access to print data.
- Biometric Authentication: Some Sharp models support biometric authentication methods, such as fingerprint recognition, for an additional layer of security.
- Authorization Policies: Administrators can create granular authorization policies, ensuring that users can only access the printer’s functions relevant to their roles.
- Kerberos and Transport Layer Security (TLS): This combination of security helps to keep documents from being intercepted by cyber thieves.
- User Authentication Methods: Sharp printers can require authentication through PIN numbers, usernames and passwords, or by ID cards.
- User Authentication Types: Other Sharp copier security measures include local user lists, LDAP, Active Directory, and External authority.
#8 Single Sign-on (SSO) to Network and Cloud Resources
Integration with an organization’s authentication infrastructure is essential for seamless and secure network and cloud access. IT administrators face challenges with maintaining security while sustaining employee productivity. Adding operational convenience while validating user access can be simplified.
- SSO Integration: Sharp printers can integrate with Single Sign-on (SSO) systems, reducing the need for multiple login credentials and simplifying access management.
- Kerberos Token-Based SSO: Administrators can secure the network with tokens.
- Microsoft Exchange Server: Compatibility with Exchange Server helps provide print security.
- SSO Cloud Services: Sharp printers support Box™, Google Drive™, OneDrive® for Business, and SharePoint® Online.
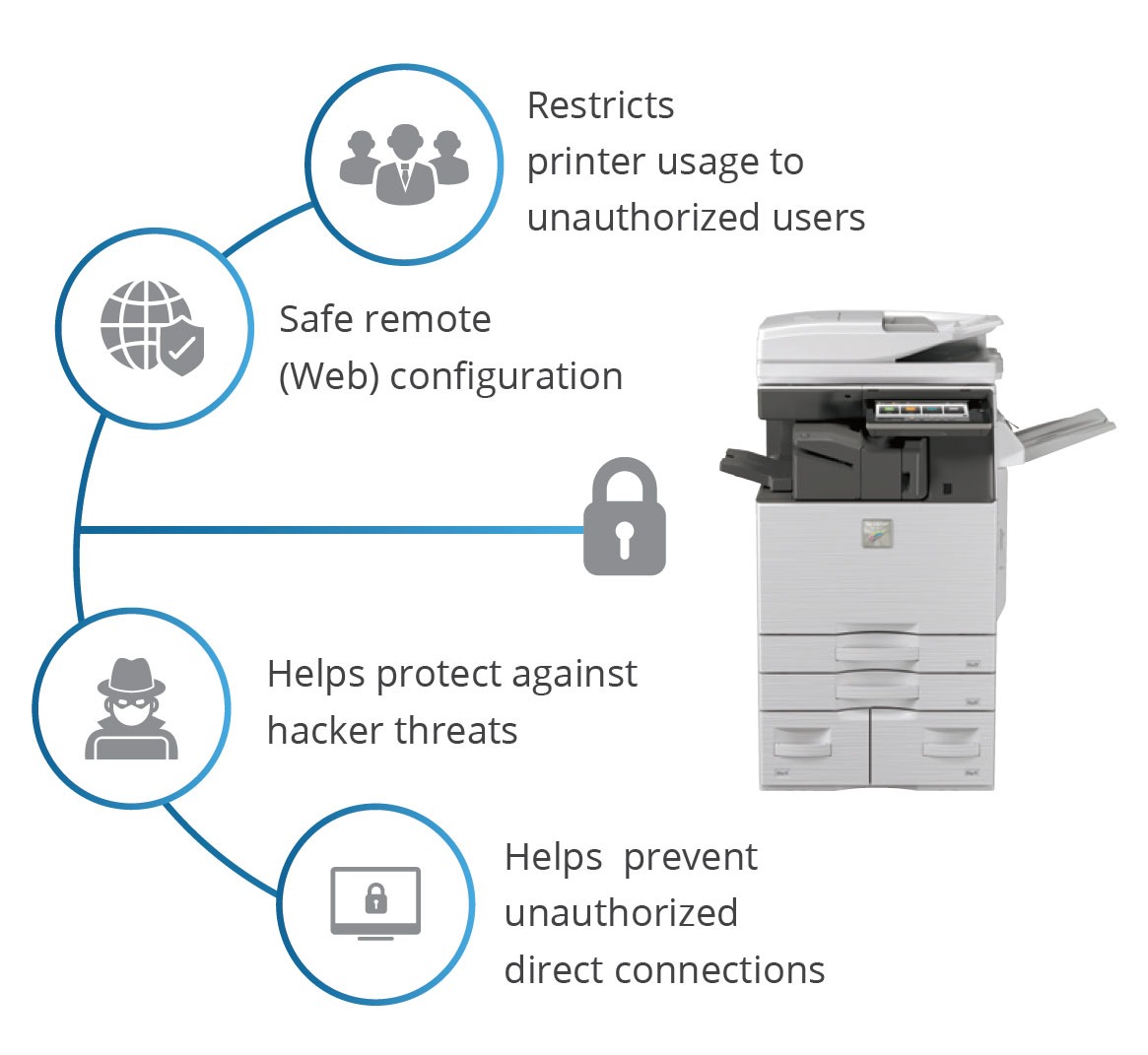
#9 Network Security
Sharp understands the importance of securing the network infrastructure from improper network use. Sharp integrates protections for intrusions, denial-of-service (DOS) attacks, and unauthorized access and alterations.
- Firewall Protection: Some Sharp printers have built-in firewalls to protect against unauthorized access and network attacks.
- Network Authentication: Sharp printers support various network authentication methods, ensuring only authorized devices can communicate.
- Authorization Protocols: Sharp employs SHA-2 certificates, Wireless LAN protection, IPv6 and SMBv3 communications, IP address and MAC address filtering, port management, CA certificates, IEEE802.1X™ authentication, and device certificates.
#10 Document Security
Protecting the content of printed documents is paramount. Sharp employs several measures to safeguard documents through encryption and other protective functions.
- Watermarking: Printers can apply watermarks to printed documents, helping to deter unauthorized reproduction.
- Document Access Control: Administrators can set access controls, restricting who can print, copy, or scan specific documents.
- Device Security: Using encrypted PDFs, pull printing, PIN printing, and secure document filing provide document security.
- Synappx Go: Sharp employs Snynappx Go technology for secure print release, print for cloud storage, scan to self or cloud, and NFC tag.
#11 Email Security
In an interconnected world, email security is a critical concern. Email is the most frequently used business communication.
- Email Encryption: Sharp’s email encryption feature ensures that email attachments, including scanned documents, remain secure during transmission.
- Email Connect: Sharp establishes a direct connection for Exchange serves of Gmail, preventing generic MFP addresses.
- Integration with Email Security Tools: Sharp printers can seamlessly integrate with third-party email security solutions for an added layer of protection.
- Digital Signature: Printers provide encryption with S/MIME.
- Destination Restriction: Administrators can regulate where employees may send emails.
#12 Mobile and Wireless Security
Mobile and wireless security is essential to prevent access by unauthorized mobile devices. Sharp protects mobile users connecting with the company network to reach printers, copiers, or MFPs.
- Mobile Printing: Sharp supports secure mobile printing solutions that enable users to print from their smartphones or tablets while maintaining security. Sharp printers adhere to the latest wireless security protocols to safeguard data transmitted wirelessly.
- User Authentication: Printers employ Active Directory, LDAP, Local User List, and PIN number.
- SNMP Security
- Serverless Print Release
#13 Audit Trail
A robust audit trail is essential for monitoring printer activity. Tracking user activities and events helps to diagnose existing problems and potential problems.
- Event Logging: Sharp printers log various events, including login attempts, printing, scanning, and configuration changes, allowing administrators to track user actions.
- Job Logging: Certain regulations require parameters, such as “to,” “from,” “when” and “file name” to be logged, reviewed, and archived for conformance.
- Comprehensive Reports: Administrators can generate comprehensive reports from the audit trail data, aiding in compliance and security investigations. Administrators can monitor events such as when and what settings changed, which IP address accessed the device, and when firmware updates.
- Supports RFC 5424/3164 Standard Syslog Protocol
#14 Print Security and IT Environment Compatibility
The design of Sharp printers seamlessly integrates into your IT environment.
- Print Queue Management: Sharp printers can be integrated with print queue management systems, ensuring that print jobs are securely processed.
- Compatibility with Security Software: Sharp printers are compatible with a wide range of security software and solutions, making it easier for organizations to manage printer security alongside other IT security measures.
- Government Compliance: Sharp complies with HIPAA and FERPA requirements.
- WHQL-certified: Microsoft-certified print driver to ensure compatibility and meet security standards in the Microsoft environments.
- Citrix-ready: Printers meet Citrix evaluation for use in Citrix environments.
- SAP-ready: Printers meet device-type requirements for SAP environments.
- Cerner and McKesson Compatibility: Printers meet healthcare application compatibility requirements for Cerner, McKesson, and other healthcare providers.
- User Authentication: Authenticates all print jobs for device acceptance.
- Serverless Print Release: Sharp MFPs release the print job when the user is at the printer.
- Sharp OSA-enable Applications: Print release and output management software with advanced security features provide user authentication, authorization, and accounting.
#15 Fax Security
Even in the digital age, fax machines remain in use, and they require security considerations:
- Fax Encryption: Sharp offers fax encryption to protect sensitive information sent via fax from interception.
- Fax Authorization: Administrators can set up authorization rules for sending and receiving faxes, ensuring only authorized users can use this feature.
- Logical Separation: Sharp provides separation between LAN and fax communications. This separation prevents cyberattacks on the internal systems of MFPs or the local network.
- Fax Protocol: The MFPs only allow the fax protocol to operate in the modem.
- UART Protection: MFP fax transmissions stay separate from UART communications to minimize the risk of transmitting malicious data and viruses.

FAQs: Printer Security and Information Security
- Why should businesses consider printer security in their overall information security plan?
Printers can be vulnerable points of entry for cyberattacks and data breaches. Securing printers is essential to protect against potential threats and maintain overall information security.
- What are the consequences of overlooking printer security in a business environment?
Overlooking printer security can lead to data breaches, non-compliance with regulations, corporate espionage, reputation damage, operational disruption, and financial losses.
- How does printer security fit into an organization’s overall cybersecurity strategy?
Printer security is an integral part of an organization’s overall cybersecurity strategy as it helps protect against data breaches and cyber threats that can impact various areas of the organization.
- What are some of the security features offered by Sharp printers to enhance information security?
Sharp printers offer a wide array of security features, including data encryption, data security kits, access control security, data security at end-of-lease, firmware updates, remote monitoring, authentication, authorization, and many more.
- How does Sharp address data security during the entire lifecycle of a printer?
Sharp printers have features such as data overwrite functions and guidelines for securely returning leased or retired devices to ensure data security from birth to the end-of-life of a printer.
- What role does audit trail play in printer security, and how does Sharp implement it?
An audit trail is essential for monitoring printer activity and tracking user actions. Sharp printers log various events, and administrators can generate comprehensive reports from this data to aid in compliance and security investigations.
- How does Sharp ensure compatibility with an organization’s IT environment and security software?
Sharp printers seamlessly integrate into IT environments, including compatibility with print queue management systems, security software, government compliance requirements, and authentication methods.
- What security measures does Sharp offer for email security and mobile and wireless security?
Sharp printers offer email encryption, integration with email security tools, Single Sign-on (SSO) support, and protection against unauthorized mobile device access to maintain email and mobile security.
- How does Sharp address network security to protect against intrusions and unauthorized access?
Sharp printers include built-in firewalls, network authentication methods, authorization protocols, and other security measures to protect against network attacks and unauthorized access.
- What security features does Sharp provide for document protection, including watermarking and secure printing?
Sharp printers offer document protection features such as watermarking, access control, device security, and secure document filing to safeguard printed documents.
- Why is fax security still relevant, and how does Sharp address it?
Fax security remains important, and Sharp offers fax encryption, authorization rules, logical separation, and other security measures to protect sensitive information sent via fax.
- What certifications and standards does Sharp adhere to in ensuring printer security?
Sharp printers have achieved Common Criteria Certification (ISO-15408) and comply with various security standards, including HIPAA and FERPA requirements.
- How can organizations benefit from implementing Sharp’s comprehensive printer security features?
Organizations can benefit from enhanced data protection, compliance assurance, prevention of data breaches, and overall improved information security by implementing Sharp’s security features.
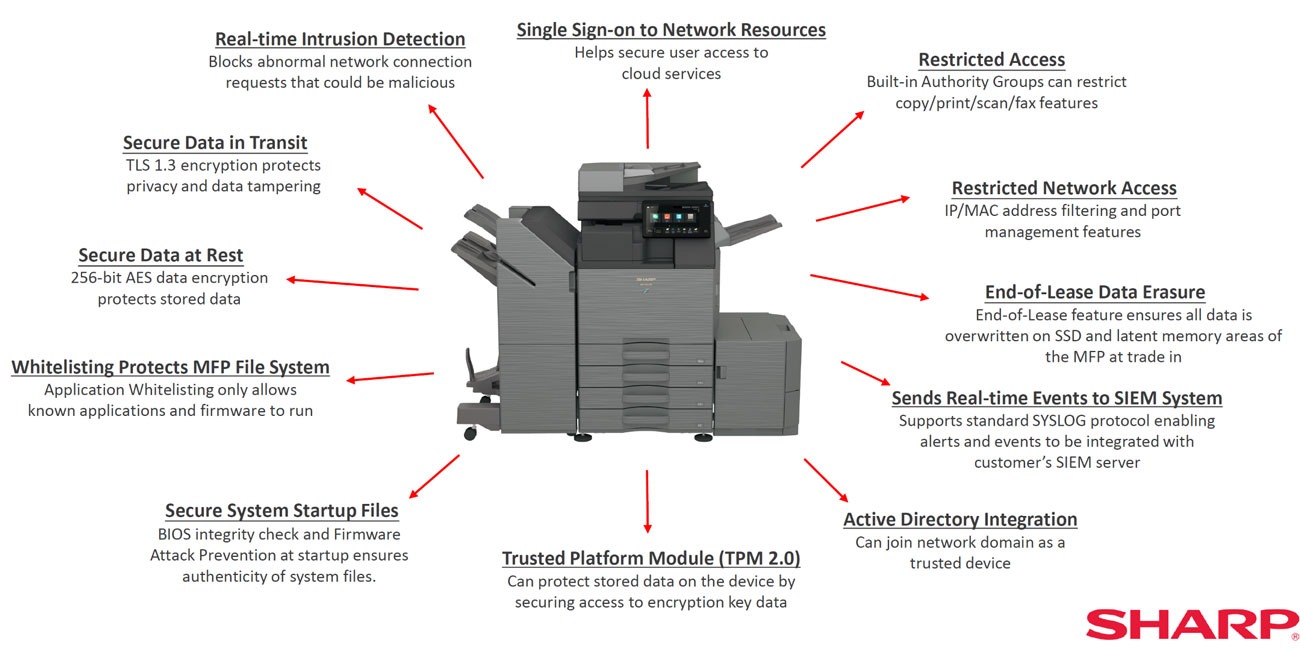 Conclusion
Conclusion
Information security is a non-negotiable aspect of modern business operations. Printers may be a minor component of an organization’s IT infrastructure. However, office printers can be a significant source of security vulnerabilities if left unprotected. From data encryption to access control, from firmware updates to audit trails, Sharp printers have the tools to protect businesses from data breaches, compliance violations, and operational disruptions. Sharp’s commitment to comprehensive information security is evident in its array of security features.
Les Olson IT is an authorized retailer of Sharp printers and copiers. Our company markets the top tier brands of office machines. We stock parts locally to Service Sharp Office Products throughout the state of Utah and in the Las Vegas area. Call us to schedule an appointment with a Sharp specialist – (801) 452-7988.
Manuals and Documents
 Sharp BP Series Printer Security – provides a 12-point printer security infographic.
Sharp BP Series Printer Security – provides a 12-point printer security infographic. Security Suite Reference Guide – offers a comprehensive description of Sharp’s printer security advantages.
Security Suite Reference Guide – offers a comprehensive description of Sharp’s printer security advantages. Heightened Security Helps Ensure Confidentiality – covers industries and their respective information security needs.
Heightened Security Helps Ensure Confidentiality – covers industries and their respective information security needs. Mitigate Threats to MFP – provides a security checklist for Sharp multifunctional printers.
Mitigate Threats to MFP – provides a security checklist for Sharp multifunctional printers. 8-Point Copier Security Infographic – contains information about Sharp printer built-in protections.
8-Point Copier Security Infographic – contains information about Sharp printer built-in protections. Did You Know? Printer Security Infographic – facts for secure office printing.
Did You Know? Printer Security Infographic – facts for secure office printing. 5 Reasons You Need a Copier Security Plan – infographic about the importance of printer security.
5 Reasons You Need a Copier Security Plan – infographic about the importance of printer security.
 Footnotes
Footnotes
- 1Rajeswar, Sundaresan. Top Business Risks for 2023. The Institute of Internal Auditors. Accessed 25 Sep. 2023. www.theiia.org/en/affiliates/IIA-Qatar/news/top-business-risks-for-2023/
- 2Kolesnikov, Nicole. 50+ Cybersecurity Statistics for 2023 You Need to Know – Where, Who & What is Targeted. Techopedia. 30 August, 2023. Accessed 25 Sep. 2023. www.techopedia.com/cybersecurity-statistics#:~:text=Cybersecurity%20Key%20Stats,was%20%244.35%20million%20in%202022
- 2 Get clued into the cyber world reality. Cybersecurity & Infrastructure Security Agency. U.S. Department of Homeland Security. Accessed 25 Sep. 2023. www.cisa.gov/be-cyber-smart/facts
- 2Page, Carly and Whittaker, Zack. Hackers claim MGM cyberattack as outage drags into fourth day. TechCrunch. September 14, 2023. Accessed 25 Sep. 2023. techcrunch.com/2023/09/14/mgm-cyberattack-outage-scattered-spider/