Why Business Cyber Security is Your Top Priority in 2026

Digital transformation shapes every aspect of modern business operations. Because of this, business cyber security has become a necessary pillar for your strategy and long-term sustainability. Since October is Cyber Security Awareness Month, we want to share the protection your data needs. Get ready as we break down the modern threat landscape. Learn how businesses […]
How to Choose a Business Server

Choosing the right server profoundly impacts your business. Les Olson IT is your business server expert, with decades of experience supporting managed technology and IT. We’re exploring server types and highlighting the factors that should drive your choice. What Is a Business Server & Why Do You Need One? At its core, a business server […]
Cybersecurity Compliance – A Guide for Businesses

In an era where digital transformation shapes every facet of business operations, cybersecurity compliance emerges as a regulatory hoop to jump through and as a cornerstone of trust, safety, and sustainability in the digital marketplace. Whether safeguarding sensitive customer data, ensuring the integrity of business processes, or protecting the confidentiality of cardholder and medical information, […]
Ranking the Top Best Printers for Cybersecurity

Network Security in the Age of IoT In today’s digital age, where data security is a paramount concern for businesses, protecting printers and other company network devices within the organization’s communication infrastructure is a critical focus. Networked devices embedded with sensors, software, and communication technologies connect and exchange information with other devices over the internet. […]
22 Cybersecurity Trends for Businesses in 2024

The business landscape witnessed a rapid surge for cyber threats in 2023, elevating Cybersecurity to a paramount concern for regional and global organizations. As we approach 2024, the cybersecurity domain is seeing several emerging trends. Cybersecurity experts advocate that the focus of viable network protection begins with people, processes, and technology.1 Companies have an advantage over […]
15 Sharp Printer Information Security Features for 2023
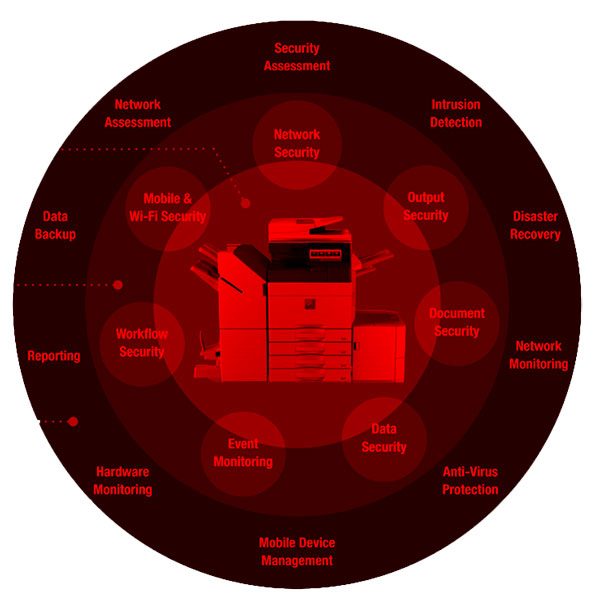
Information transfer is a significant part of business and organizational communications in today’s digital age. Mobile and cloud integrations with office technologies increase the complexity and frequency of protecting business information. Corporate information, customer data, client privacy, and financial information are constantly under threat by interception and misuse. Data security is critical for businesses of […]
Cybersecurity Compliance with FTC Safeguard Rules

Business compliance with the upcoming FTC Safeguards Rules deadline! Nine new standards for cybersecurity and why they are crucial for consumer privacy and data security.
Cybersecurity in the Home

In this increasingly wireless world, the steps households should take in terms of cybersecurity have changed. Most homes now run networks of devices linked to the internet, including computers, gaming systems, TVs, tablets, and smartphones that access wireless networks.
4 Tips to Keep Your Business Safe and Secure

Keeping information safe and secure is challenging developments for businesses of all sizes over the last few years. Expeditious shifts from in-person to online to hybrid workplaces forced companies to change, or at least reexamine, their cybersecurity practices and protocols, and far too often they weren’t prepared.
Data Breach Anatomy: What Are They and What to Do?

How to spot a possible breach? The best way to stop a data breach is to stop it before it even starts. This includes taking steps from making sure passwords are long and complex to report suspicious emails. If you do suspect that you have been the victim of a breach, immediately contact your IT department or device provider to notify them and follow subsequent protocols to help them scan, detect, and remediate any issues that exist.
Concerned About Cyber? 4 Easy Steps for Staying Secure in 2022

Cybersecurity has become one of the biggest hot topics both inside and outside of technology circles over the last two years. From securing learning devices due to a rise in digital learning during the COVID-19 pandemic to coping with the fallout of high-profile breaches of national infrastructure such as the Colonial Pipeline, there is a seemingly endless news cycle dedicated to cybersecurity mishaps and concerns.
Cybersecurity Awareness Month Champions

Building on annual success Cybersecurity Awareness Month 2022 is set to highlight the growing importance of cybersecurity in our daily lives and look to empower everyday individuals and business to take cybersecurity steps by making cyber more accessible









