CyberSecurity

March 22, 2024
In an era where digital transformation shapes every facet of business operations, cybersecurity compliance...

March 7, 2024
IT Services IT services consist of a one-time project by professional IT experts limited in project length....

December 7, 2023
Printer Vulnerability Multifunction printers (MFPs) are pivotal tools within contemporary offices, optimizing...

December 7, 2023
Network Vulnerability Due to Printers In the modern business landscape, network printers play an integral...

December 5, 2023
Overlooked Printer Security In today’s digital age, where data breaches and cybersecurity threats...

November 29, 2023
Network Security in the Age of IoT In today’s digital age, where data security is a paramount concern...

October 16, 2023
The business landscape witnessed a rapid surge for cyber threats in 2023, elevating Cybersecurity to...
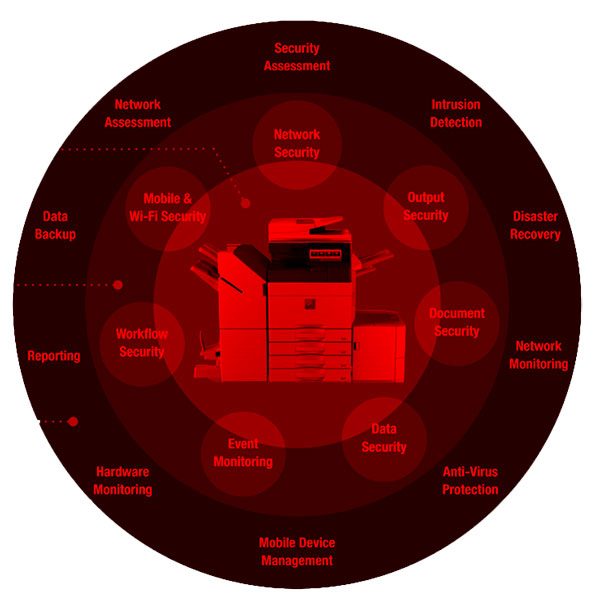
September 26, 2023
Information transfer is a significant part of business and organizational communications in today’s...

September 7, 2023
Cybersecurity statistics indicate that electronic threats are significantly on the rise. Business email,...

August 8, 2023
Safeguarding Sensitive Health and Financial Information When providing IT Services, different industries...

December 28, 2022
Business compliance with the upcoming FTC Safeguards Rules deadline! Nine new standards for cybersecurity...
No posts found


